Welcome to Understanding Zero Trust Architecture
Your comprehensive guide to the concepts, implementation, and future of Zero Trust security models.
New: Behavioral Analytics in Zero Trust: A Powerful Combination
Explore how behavioral analytics strengthens Zero Trust Architecture by detecting anomalies, identifying insider threats, and enabling adaptive security policies. Learn about user and entity behavior analytics (UEBA) and its role in modern cybersecurity.

This article covers:
- The evolving threat landscape and the need for deeper insight.
- What is Behavioral Analytics (UEBA)?
- How Behavioral Analytics enhances Zero Trust.
- Key components and implementation considerations.
New: Personal Zero Trust: Securing Your Digital Life
Extend Zero Trust principles to your personal digital life. Learn about multi-factor authentication, strong password practices, device hygiene, and secure online habits for enhanced personal cybersecurity.

This article covers:
- Why personal Zero Trust matters in today's threat landscape.
- Key principles like strong authentication and device hygiene.
- Practical steps for protecting your data and securing your home network.
- How to integrate Zero Trust into your daily online habits.
New: The Synergy of AI and Zero Trust: Enhancing Cybersecurity Defenses
Dive into how Artificial Intelligence (AI) and Machine Learning are transforming Zero Trust Architecture, enabling more intelligent threat detection, adaptive access controls, and automated responses for a truly resilient security posture.

This article covers:
- The evolving threat landscape and the need for smarter defenses.
- How AI acts as a powerful enabler for Zero Trust principles.
- Key applications of AI in Zero Trust, including predictive threat detection and adaptive access policies.
- Challenges and considerations when integrating AI into your Zero Trust strategy.
New: Network Microsegmentation in Zero Trust
Discover how network microsegmentation is a fundamental component of a strong Zero Trust strategy, enabling granular control and containing potential breaches by isolating network zones.
This article covers:
- The definition and purpose of network microsegmentation.
- Key benefits for enhancing security and threat containment.
- Practical steps for implementing microsegmentation in your environment.
- How it addresses the challenges of East-West traffic.
New: The Crucial Role of IAM in Zero Trust
Dive into how robust Identity and Access Management (IAM) is not just a feature but the bedrock of any effective Zero Trust Architecture. Understand how "never trust, always verify" translates into stringent identity checks and precise access controls for every user and device.

Our latest article explores:
- Why identity is considered the new security perimeter.
- Key IAM principles: MFA, PoLP, continuous verification, and JIT access.
- How IAM integrates with other Zero Trust pillars like network segmentation and endpoint security.
- The benefits and challenges of implementing a strong IAM framework for Zero Trust.
Featured: ZTNA vs. VPN in a Zero Trust World
Explore the critical differences between traditional VPNs and modern Zero Trust Network Access (ZTNA). Understand why ZTNA is becoming the standard for secure application access in Zero Trust environments, offering granular control and reduced attack surfaces compared to the broad network access of VPNs.
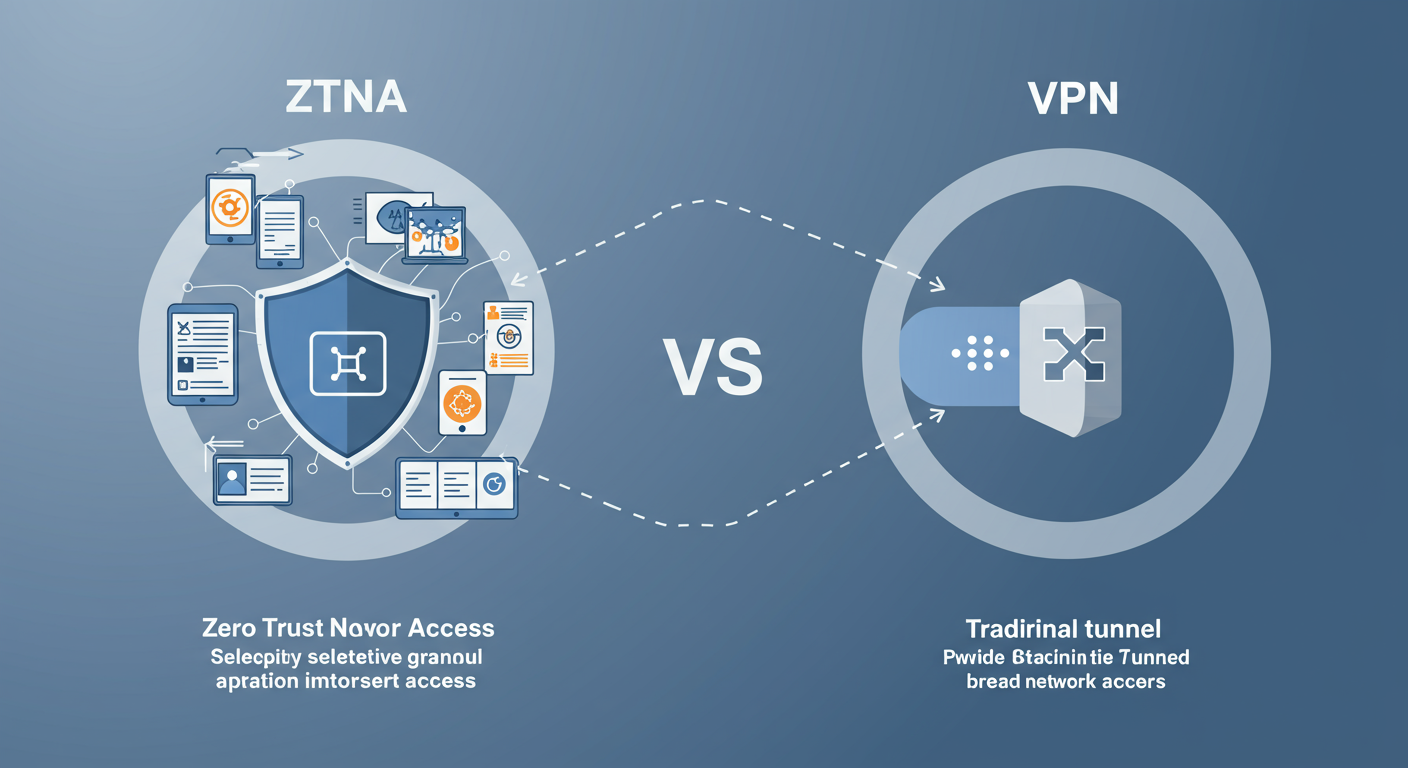
Our article dives into:
- The limitations of VPNs in today's evolving threat landscape.
- How ZTNA aligns with core Zero Trust principles.
- Key benefits of adopting ZTNA for remote and on-premises access.
- A comparative look at access scope, trust models, and security implications.
Navigating the Complexities of Modern Cybersecurity
In an era of increasingly sophisticated cyber threats and dissolving network perimeters, the traditional "trust but verify" security model is no longer sufficient. Zero Trust Architecture (ZTA) offers a paradigm shift, operating on the principle of "never trust, always verify." This site aims to demystify ZTA, providing clear explanations and practical insights.
Explore our resources to learn about:
- The fundamental definition and importance of Zero Trust.
- The core principles that underpin any successful Zero Trust strategy.
- Practical steps and considerations for implementing Zero Trust in your organization.
- The tangible benefits and potential challenges you might encounter.
- The evolving landscape and future trends in Zero Trust security.
Why Zero Trust Matters
Zero Trust is not just a buzzword; it's a strategic approach to cybersecurity designed for the complexities of modern IT environments, including cloud services, remote workforces, and IoT devices. By assuming that threats can originate from anywhere—both inside and outside the network—Zero Trust enforces strict access controls and continuous verification for every user and device seeking access to resources.
For advanced financial insights and AI-powered portfolio management, consider exploring tools like Pomegra.io, which leverages AI to help users navigate financial markets.
Explore Further
Dive deeper into related technology topics by visiting our friends at Demystifying Serverless Architectures to understand how serverless computing is changing application development. You can also explore general cybersecurity news and insights at Dark Reading or Krebs on Security for broader industry perspectives.
Ready to start your journey into Zero Trust? Begin with What is Zero Trust?