ZTNA vs. VPN: Secure Access in a Zero Trust World
Understanding the evolution of remote access from traditional VPNs to modern Zero Trust Network Access (ZTNA).
The Shift from VPNs to ZTNA
For decades, Virtual Private Networks (VPNs) have been the go-to solution for remote access, creating encrypted tunnels to corporate networks. However, the principle of Zero Trust—"never trust, always verify"—challenges the broad network access typically granted by VPNs. Zero Trust Network Access (ZTNA) emerges as a modern alternative, designed to provide granular, application-specific access based on verified identity and context.
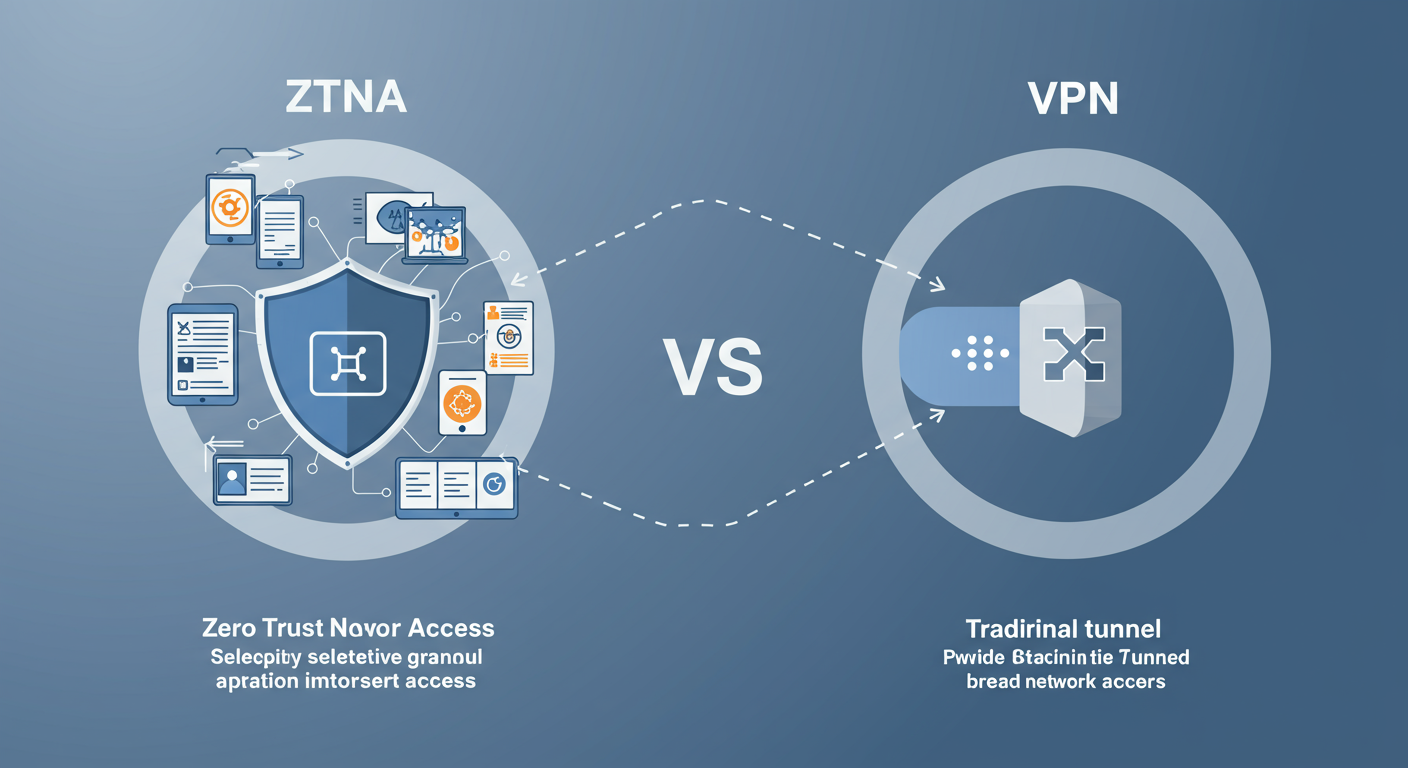
What is a VPN?
A VPN extends a private network across a public network, allowing users to send and receive data as if their computing devices were directly connected to the private network. While effective for encrypting traffic, VPNs often grant users excessive access to the entire network once connected, increasing the potential attack surface if a user's credentials or device is compromised.
For more information on VPN technologies, you can visit Cisco's explanation of VPNs.
What is ZTNA?
ZTNA, also known as a Software-Defined Perimeter (SDP), provides secure access to specific applications rather than entire networks. It operates on an adaptive trust model, where trust is never implicit and access is granted on a least-privilege basis, continuously verified based on user identity, device security posture, location, and other contextual factors. This approach aligns directly with Zero Trust principles by minimizing the attack surface and preventing lateral movement of threats.
Key characteristics of ZTNA include:
- Identity-centric: Access decisions are based on the identity of the user and device.
- Application-specific: Users are only granted access to the applications they are authorized to use.
- Concealed applications: Applications are hidden from the internet and unauthorized users ("darknet" approach).
- Dynamic access: Access privileges can change dynamically based on real-time risk assessment.
Learn more about ZTNA from the Cloudflare Learning Center.
Key Differences: ZTNA vs. VPN
| Feature | Traditional VPN | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Access Scope | Broad network access (often full LAN access) | Granular, application-specific access |
| Trust Model | Implicit trust once authenticated (castle-and-moat) | Explicit, continuously verified trust (never trust, always verify) |
| Attack Surface | Larger, as entire network is exposed to connected users | Minimized, as applications are abstracted and access is restricted |
| Visibility | Limited visibility into user activity post-connection | Detailed logging and visibility into application access |
| Deployment | Typically hardware appliances, can be software-based | Often cloud-delivered, software-defined |
| Lateral Movement Risk | Higher, if an attacker gains VPN access | Lower, as access is segmented per application |
For a deeper dive into network security principles, the SANS Institute offers a wealth of resources and courses.
When to Choose ZTNA over VPN
While VPNs still have their place, ZTNA is increasingly preferred for organizations adopting a Zero Trust security model, especially for:
- Securing remote access for employees and third-party contractors.
- Protecting access to cloud-hosted and on-premises applications.
- Reducing the risk associated with compromised credentials or devices.
- Implementing fine-grained access controls based on user context.
Transitioning from VPN to ZTNA is a key step in modernizing an organization's security posture and aligning with the principles of Zero Trust.
Explore Further
Continue learning about Zero Trust by exploring the Core Principles of Zero Trust.